Intrusion Detection : The Intrusion Detection System And External Internal Network Intrusion Download Scientific Diagram
Electronic intrusion detection systems on the other hand are. This gives you the opportunity to react to the intruders access attempts and prevent the attack.

Intrusion Detection Techniques For Mobile Cloud Computing In Heterogeneous 5g Gai 2016 Security And Communication Networks Wiley Online Library
Real Time Advanced Protection For All Your Devices.
Intrusion detection. An Intrusion Detection System IDS is a monitoring system that detects suspicious activities and generates alerts when they are detected. An Intrusion Detection System IDS is a system that monitors network traffic for suspicious activity and issues alerts when such activity is discovered. It is a software application that scans a network or a system for harmful activity or policy breaching.
Ad All-In-One Network Protection. Request A Demo NGFW Buyers Guide. Intrusion detection is the process of monitoring the events occurring in a computer system or network and analyzing them for signs of possible incidents which are violations or imminent threats of violation of computer security policies acceptable use policies or standard security practices.
IDS control and indicating equipment CIE - the brains which will audit and control the system. An IDS issues alerts when such activity is discovered which is then. Spend Less Time On Alerts Small Tasks And Focus On Big Picture Security For Your Team.
Spend Less Time On Alerts Small Tasks And Focus On Big Picture Security For Your Team. Host-based intrusion detection systems. In reality intrusion detection has always been a lot more than this.
30 Day Money Back Guarantee. Request An Online Demo. SnortSnarf is a program that was designed for use with Snort a security program used mainly with Linux networks.
The first host-based. At a base level intrusion detection is really the ability to detect report and facilitate remediation of access to corporate systems services and resources by unauthorised or illegitimate users. The intrusion detection system will normally be designed to provide the earliest possible warning of an intrusion attempt.
The intrusion detection method proposed by Michailidis et al. An intrusion detection system IDS is software that automates the intrusion detection process. Ad Best Free Antivirus Software Review 2021.
Compare Best Antivirus Reviews 2021. CPNI assured IDS will always consist of at least two separate components. Protect Your PC From Viruses Online Threats.
Physical security serves to prevent or at least delay entry. Ad All-In-One Network Protection. Securing a premises or area against unauthorised entry requires physical protection using suitably robust fences barriers walls and doors etc.
Simplify your network performance monitoring troubleshooting. Intrusions in this sense can be defined as any type of unauthorized access with the potential to harm the confidentiality integrity and availability of data. Intrusion detection systems monitor and analyse all network activity in order to detect unusual traffic and inform the user of any unusual activity.
Intrusion Detections Systems IDS are sited within a building and offer out of hours protection when the building or buildings are locked at night. This includes the most common method of intrusion using valid organisation account credentials to access resources for which. Start a secure free trial.
During the training phase PSO is executed recursively to calibrate the weights of the ANN. There is a difference between host-based and network-based attack detection methods. See Who is Our 1 Free Antivirus.
Request An Online Demo. Ad Auviks cloud-based network monitoring software automates complex network tasks. An intrusion detection system therefore is a tool that monitors network traffic for potential intrusions that may indicate malicious activity or a breach of policies.
Ad Top-Rated Antivirus Software. Intrusion detection is a difficult problem and in general PSO-based IDSs are normally hybrid systems where PSO is used in combination with other machine-learning techniques. MIC 08 uses PSO to train an artificial neural network ANN.
SnortSnarf converts the data from Snort into. Based upon these alerts a security operations center SOC analyst or incident responder can investigate the issue and take the appropriate actions to remediate the threat. Any malicious venture or violation is normally reported either to an administrator or collected centrally using a security information and.
Intrusion Detection Software Ids Security System Solarwinds

Pdf Intrusion Detection Systems Semantic Scholar
Github Shauryanegi Network Intrusion Detection System With The Enormous Growth Of Computer Networks Usage And The Huge Increase In The Number Of Applications Running On Top Of It Network Secrity Is Becoming Increasingly More Important
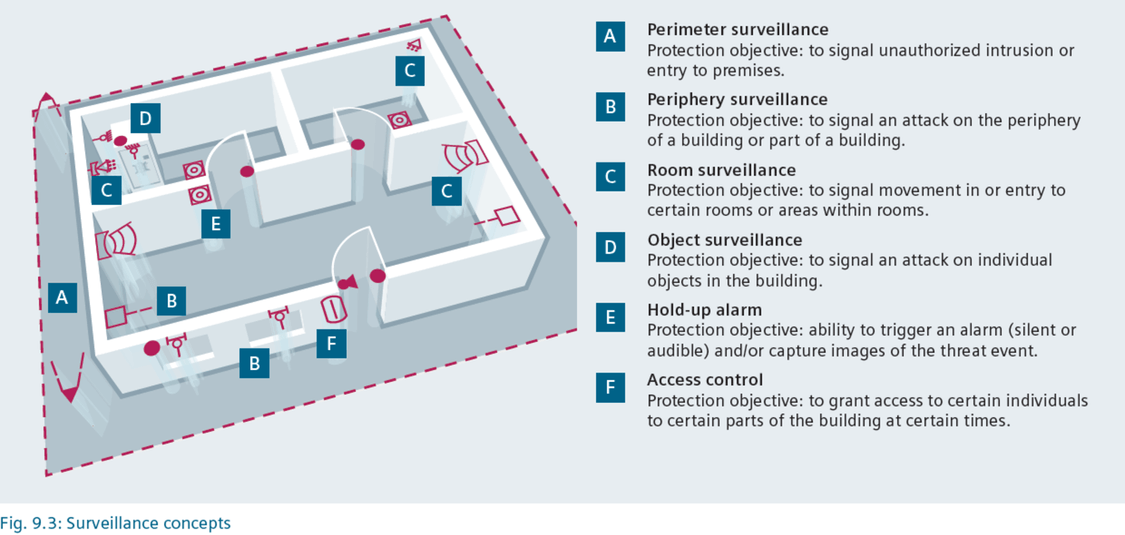
Intrusion Detection Security Siemens Global
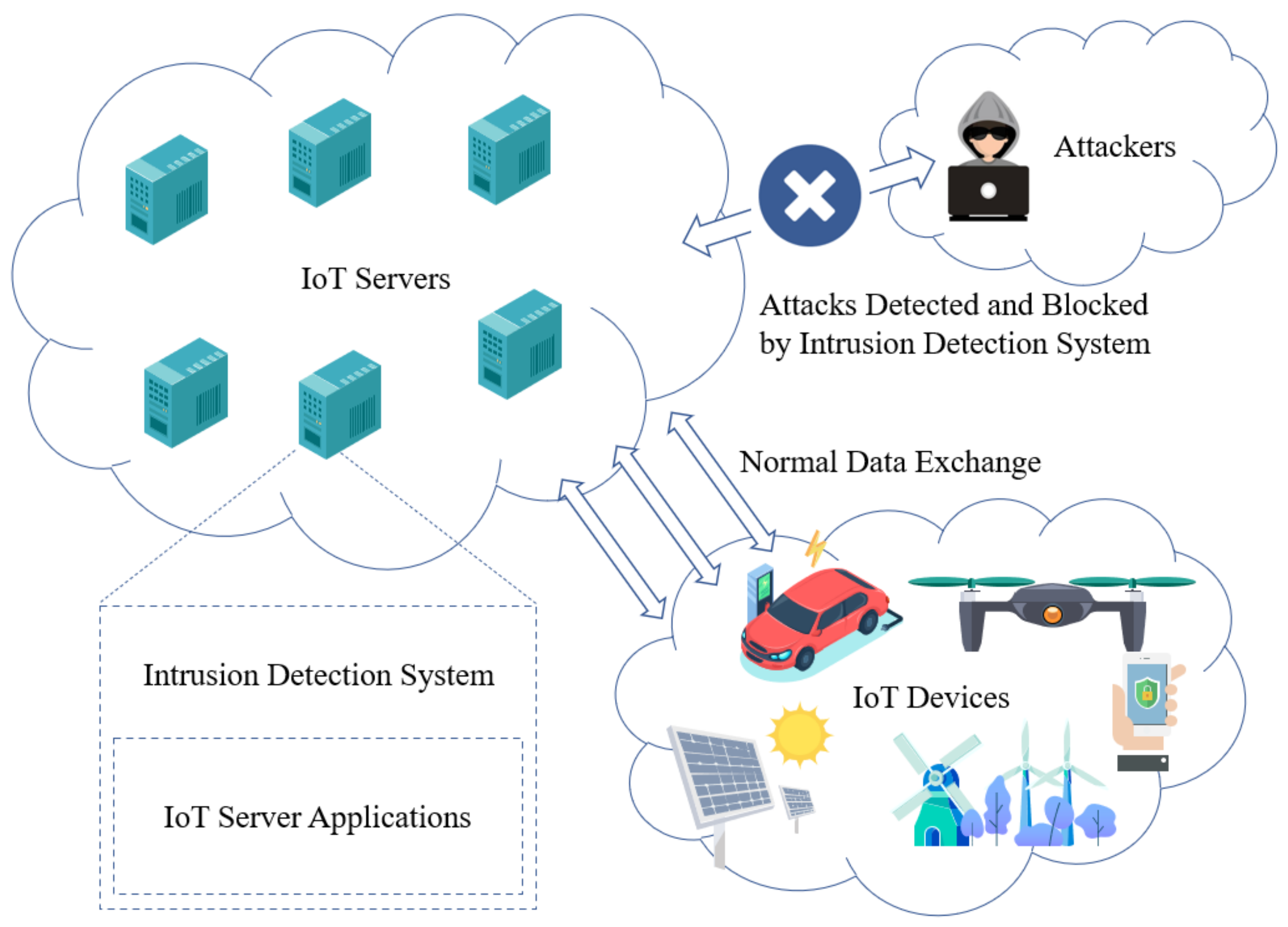
Sensors Free Full Text Sequential Model Based Intrusion Detection System For Iot Servers Using Deep Learning Methods
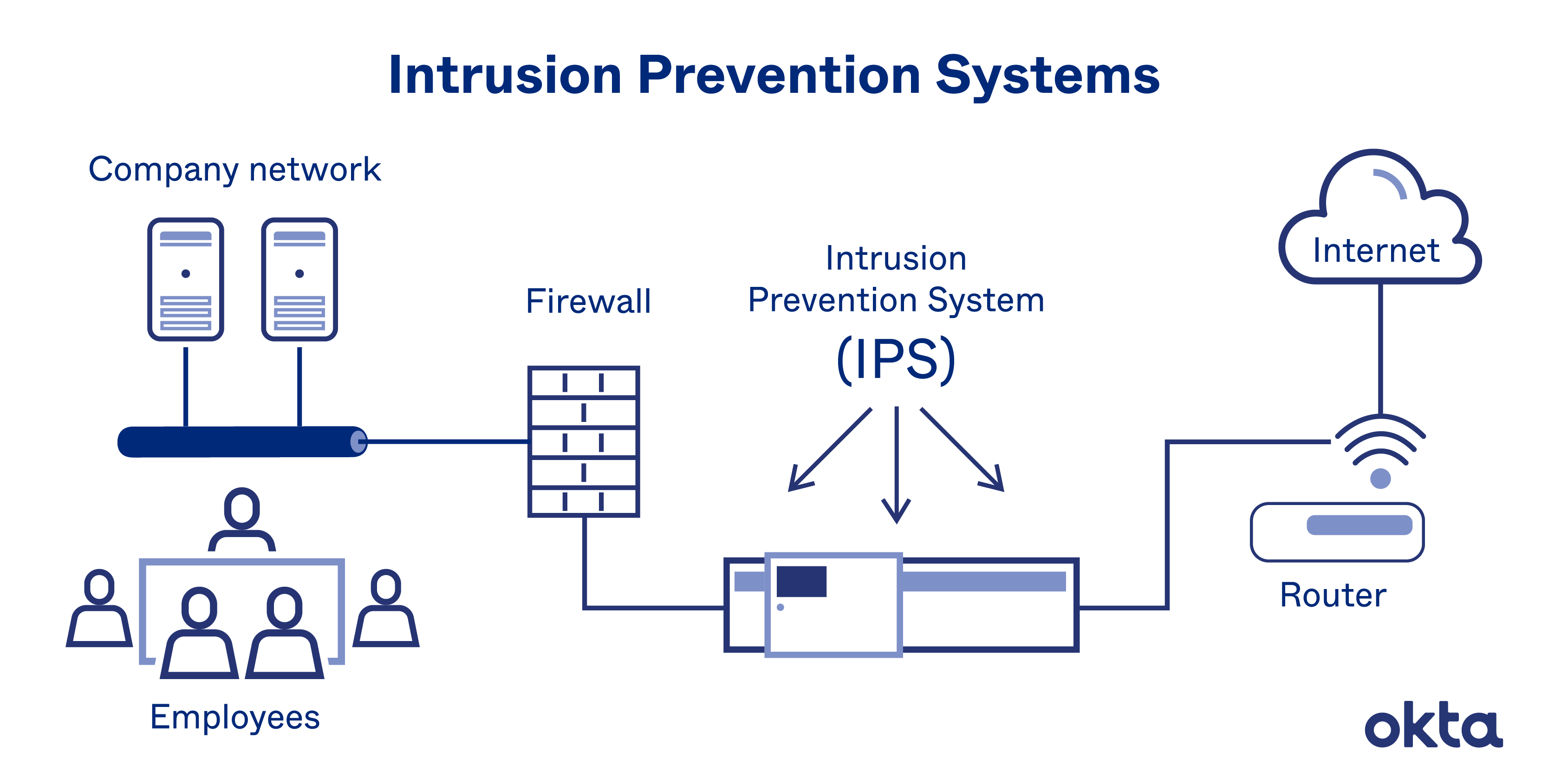
Intrusion Prevention System What Is An Ips How Do They Work Okta

What Is Ids Or Intrusion Detection System And How Does It Work The Security Buddy
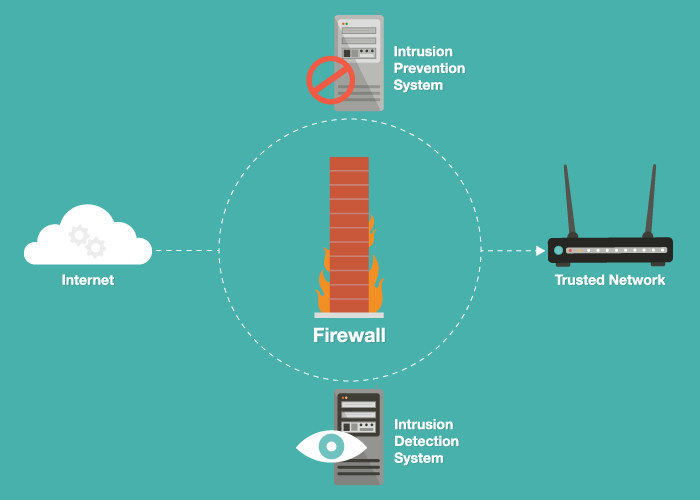
What Type Of Intrusion Detection And Prevention System Do I Need
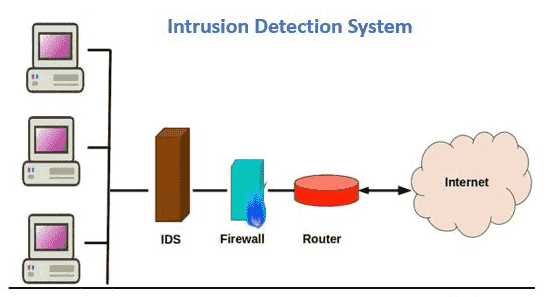
Ids In Security What Is Intrusion Detection System And Functions
Noch Etwas Zu Zero Trust Das Cloudflare Intrusion Detection System

Intrusion Detection Prevention Deciso B V Securing Networks

Intrusion Detection System Ids Ids Are Classified According To The Download Scientific Diagram
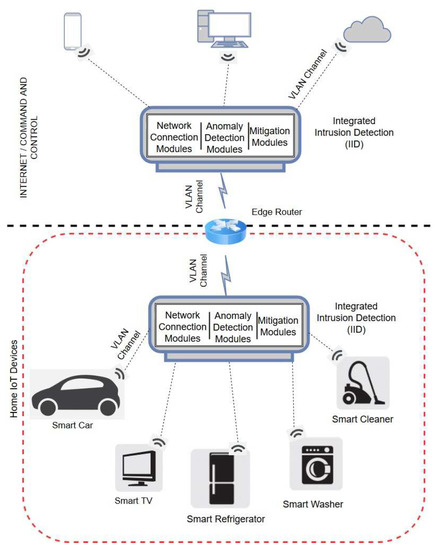
Sensors Free Full Text Towards Deep Learning Driven Intrusion Detection For The Internet Of Things
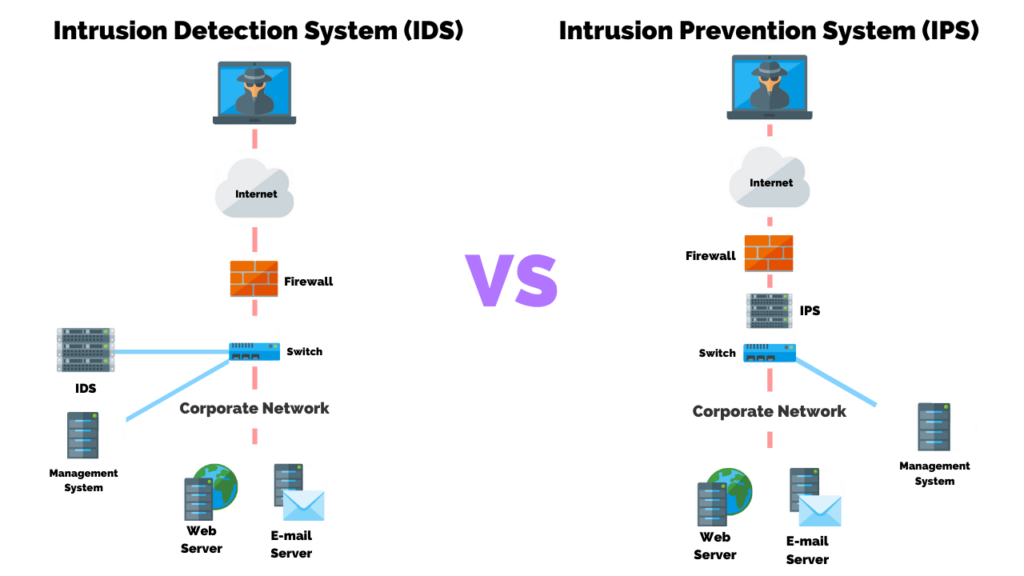
What Is The Difference Between Ids And Ips Purplesec

Building An Intrusion Detection System Using Deep Learning By Tamim Mirza Towards Data Science

Intrusion Detection Intrusion Prevention And Antivirus The Differences

Www Ips Analytics Com Ips Intrusion Detection

The Intrusion Detection System And External Internal Network Intrusion Download Scientific Diagram

Ids Intrusion Detection Systems Cissp Free By Skillset Com Youtube
